Test Methodology and Tools
This Series of articles explain How to use emerging technologies such as NFV (Network Functions Virtualization) to secure your network and adapt promptly to security threats such as DDoS attacks.
After we covered the problem statement, and requirements in the first article; we continued with the Architecture and Design Considerations in the second article. For more information please refer to the following links FIRST ARTICLE, and SECOND ARTICLE.
In this article, we will continue what we have started, and illustrate test methodology & the exact tools that was used to build the solution and the interaction between all these tools to deliver a modular setup that can be extended to deliver different options for DDoS mitigation.
Next Article will explain the tests outcome and our findings.
Mitigation Methodology
The below diagram outlines the basic network setup before launching the attack and the normal traffic flow
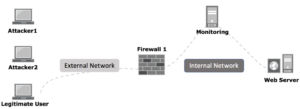
On the external network, we have a mix of legitimate users as well as attack machines that will be used to launch the DDoS attack, we have a firewall which is sites between the External and Internal network to protect the Web server and we have a monitoring station which is monitoring the health of the web server and will be used to inspect the traffic.
All the above nodes are Linux VMs which is running Ubuntu 16.04 and are onboarded on the Openstack and the above two networks are Openstack networks used to construct this topology.
The following section will outline the testing procedures that was carried in order to verify the correct mitigation for the DDoS traffic and the various methods that can be used to customize the solution
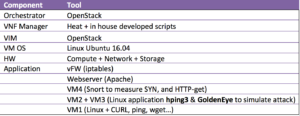
Tools
Below table presents the tools we used in our test, for webserver we had two flavours:
- Small VM used in normal cases when CPU and/or Memory utilization is less than 70% utilized.
- Large VM used when CPU and/or Memory exceed utilization 70% utilized.
1.1 Testing Setup
As we outlined in the previous post the focus of this test lab is to demonstrate the following:
- Automatic Scaling of the resources in reaction to a specific trigger.
- Ability to initiate a VNF in reaction to a specific trigger.
- Deploying a VNF with Day Zero configuration to stop DDoS attack.
- Injecting Configuration on an existing VNF to stop DDoS attack.
As we mentioned before all the above setup is simulated using Linux machines and the firewall is a simple Linux machine with iptables rules that is used to simulate a firewall.
The below steps were used to achieve the above-mentioned goals and to demonstrate the effectiveness of the solution.
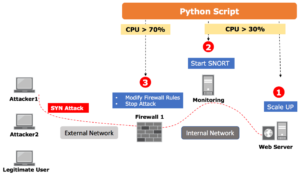
- From the attacker machines, we start the DoS attack using Hping (to simulate Syn Flood attack) or GoldenEye (to simulate HTTP GET attack).
- The monitoring station is monitoring the CPU of the web server and once the CPU exceeds 30%, the python script performs two actions
- triggers a Scale up for the resources of the web server (increase the CPU and RAM for the servers) by initiating a REST call to the Heat API of the openstack to perform this operation.
- Start SNORT (Open Source DPI) on the monitoring station to detect any malicious activity.
Note
At this point the python script is simulating both an EMS which is monitoring the VNF (the web server is the VNF in our case) and as well an NFVO and VNFM which receives the trigger from the EMS and performed a Scale UP for the resources (VNFM) and as well triggered the creation of a new service (DPI) [in our case we only started the DPI and didn’t create a complete new VNF]
- Then the python script continues to monitor the CPU for the web server as well as the SNORT logs to check for any DDoS attack. Once the CPU of the web server exceeds 70% the python script performs the following actions
- In case the attack is a SYN flood attack, the python script collect the sources of the attack from the SNORT logs and update the IP tables rules on Firewall1 to stop the SYN Flood DDoS attack on Firewall1. The below diagram outlines the network setup in case of DDoS SYN attack.
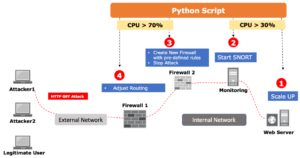
- In case the attach is a HTTP GET attack, the python script instantiates a new Firewall (a Linux machine) and populates its Iptables rules with the sources of the DDoS attack to stop it. The below diagram outlines the network setup in case of DDoS HTTP GET attack.
Note
At this point the python script is simulating both an EMS which is monitoring the VNF (the DPI at this point and collecting its logs) and as well an NFVO which receives the trigger from the EMS and communicate with the VNFM (the python script as well) to create a new VNF (firewall-2) [NFVO send the request to VNFM which deploy the VNF on the VIM]
Test Cases
We have conducted two test cases to simulate DDoS attacks:
- DDoS using TCP SYN flood
- DDoS using HTTP-Get flood
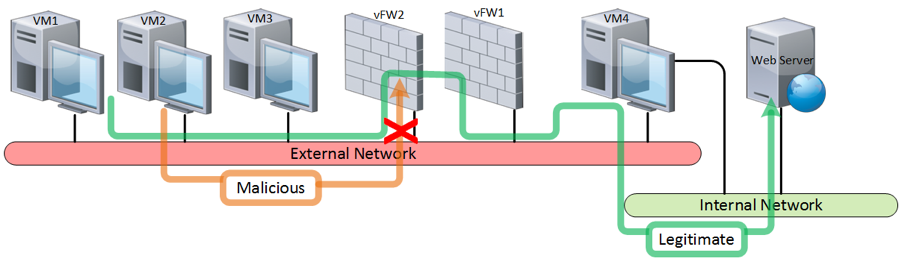
Traffic flow of DDoS attack and legitimate user traffic before mitigation is highlighted in below diagram:
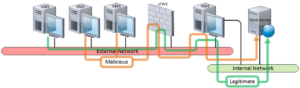
Traffic flow of DDoS attack and legitimate user traffic during the mitigation is highlighted in below diagram:
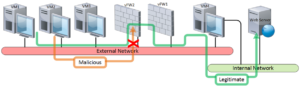
The below diagram outline the actions that will occur in case of a SYN flood attack
The below diagram outline the actions that will occur in case of a HTTP GET attack
In the next article, we will explain in details above steps and will reveal the tests outcome and our findings
Stay Tuned !!