In this series of posts, we will explore the different networking solutions offered by AWS and how to build robust and highly available cloud solutions using the native Networking services offered by AWS.
In this post, we will explore the basic building blocks of AWS infrastructure, and how AWS global network was built.
The first things to understand are:
- how AWS structure and segment its global backbone network?
- and how AWS services are offered across the globe.
The below diagram outlines the current Network Infrastructure backbone that compromises the global AWS Network and outlines the two main definitions within AWS which are a Region and an Availability Zone.
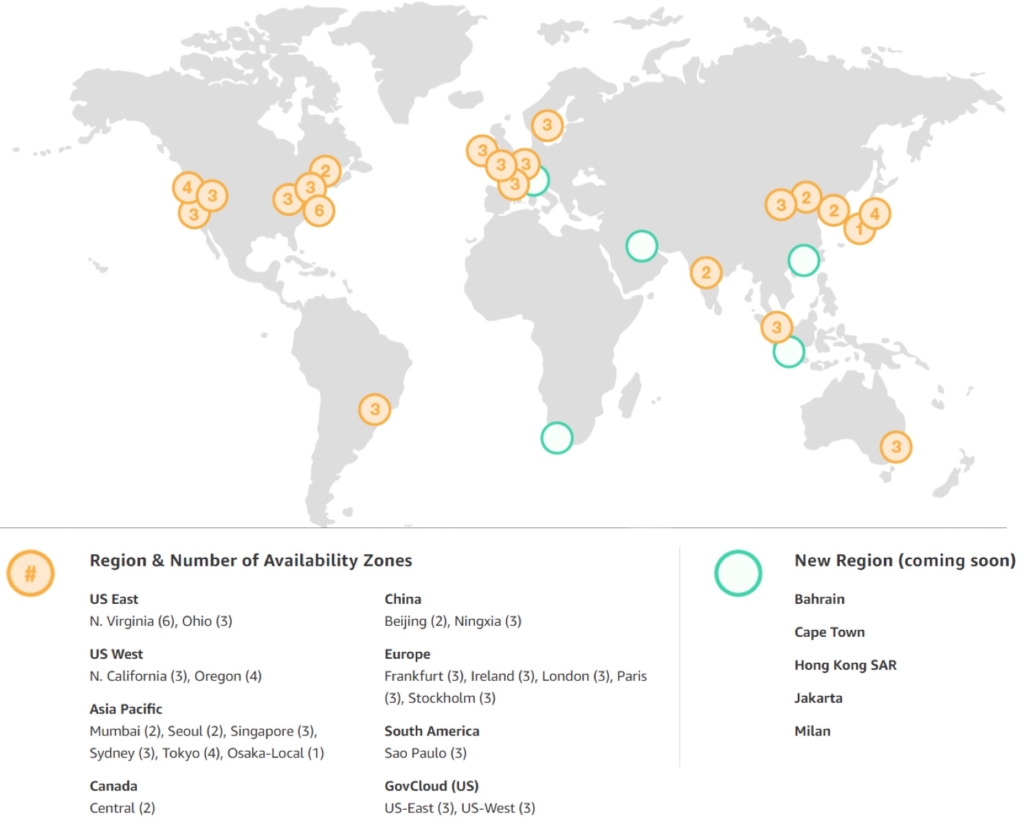
AWS Region
The highest grouping level of AWS infrastructure is called a Region, it is defined as a completely isolated collection of AWS services which AWS operates. It has the following main characteristics.
- It is completely self-contained from the other regions that AWS operate around the globe, each region is unique in terms of the following aspects
- Administration
- Finance,
- Legal, each region operate under the laws of the country which house this region, like who to deal with sensitive user date and how to classify user data.
- Compliance, each region has different compliance requirements based on the country that house this region.
- AWS services availability differ from one region to another (for example AWS managed Kubernetes service (EKS) is not available in all regions).
From a Customer point of view, the user sees the AWS Cloud as segmented into multiple locations (Regions) and the user must choose on which region to deploy and consume the different AWS services. So most of AWS services are Scoped per region, which means that in order to use any Service in AWS (whether it is Compute or storage or any other service), this service must be assigned to a specific location and as outlined before the prices for these different services vary from one Region to another. The below diagram outline the logic described above.
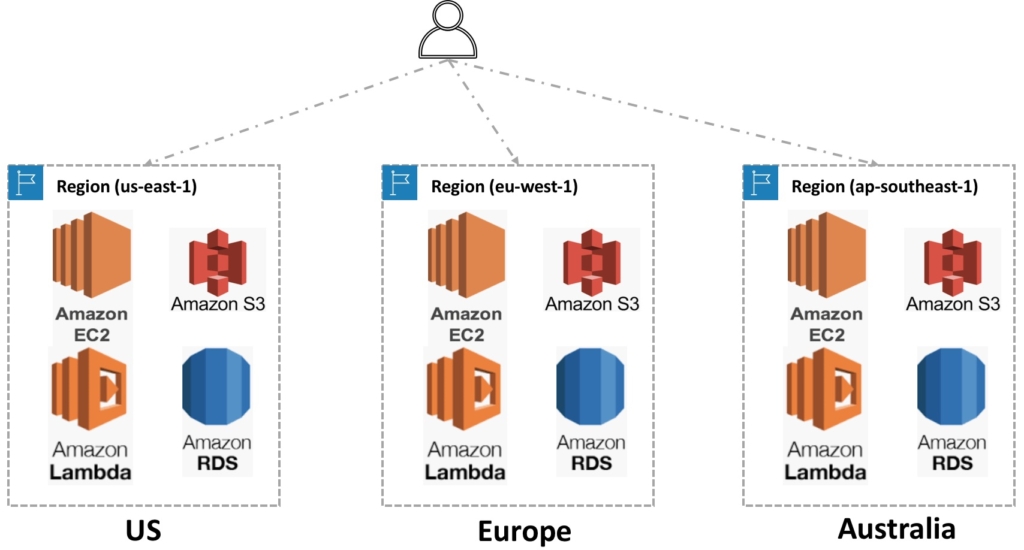
Availability Zone
After understanding the logic of a Region and how most of AWS services are scoped per region, a question must arise of how AWS provide Redundancy for its different services ?.
The answer to this question is Availability Zones, a single Region is separated into multiple Availability Zones and each Availability Zone (AZ) is considered a fault domain on its own. All the availability zones within a region are connected by very High speed, low latency links (AWS target a 2 msec latency between AZ in a region). The below diagram outlines the high-level interaction between a region and AZs.
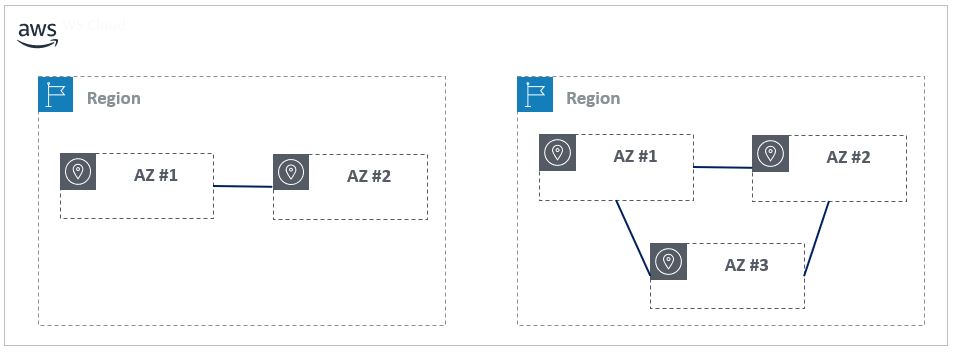
A region is composed of two or more availability zones, how an availability zone is really structured is not published by AWS so an Availability Zone can be a single physical location (DC/PoP) or multiple Data Center sites. AWS has engineered each availability zone with a different risk profile in terms of power distribution, flood location, and tectonics.
VPC
Both Regions and Availability Zones are common to all users and AWS accounts, so how can we achieve multi-tenancy in AWS in terms of Networking and IP address allocation?.
This is achieved using Virtual Private Cloud (VPC), Each User/Organization is allocated a dedicated VPC in each region by default in order to place all of its computing resources. We can think of a VPC as a virtual DC that a user has complete control over it in terms of IP address allocation (a VPC support both IPv4 and IPv6 addresses), Subnet addressing, routing and network gateways. The below diagram outline the interaction between a VPC and a region.
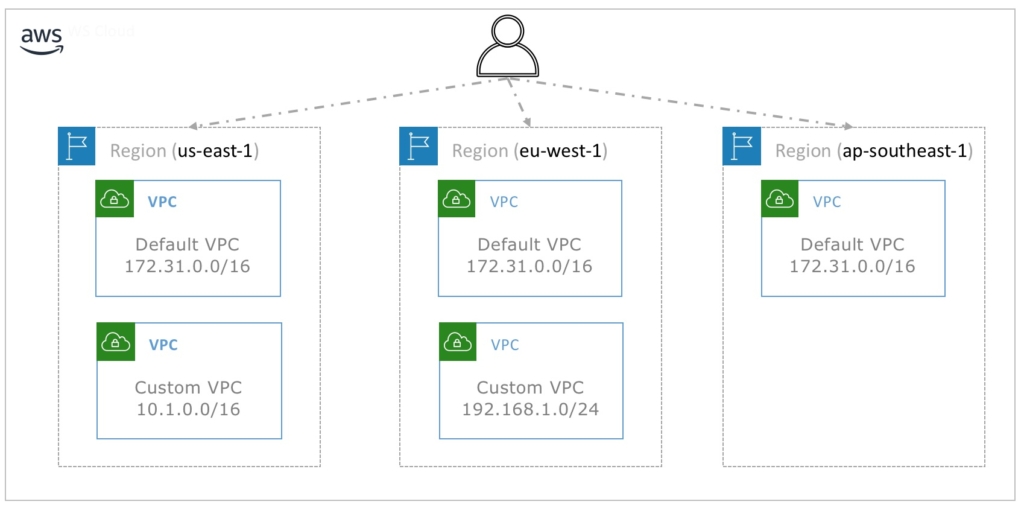
In terms of how the different VPCs communicate with each other wither within the same region or between different regions, this requires more advanced networking techniques like VPCs peering or transit VPCs, which will be discussed in a another post.
From a Scalability point of view, a User/account can have multiple VPCs per region with a minimum of one VPC per region which is the default VPC that AWS provision for each account. AWS has created the default VPC in order to ease the onboarding of resources for users with minimum networking experience and all the default VPCs in all region have the same IPv4 CIDR block of 172.31.0.0/16.
Below is a summary of the main characteristics of VPC
- VPCs are Region Specific
- We can have one or more VPCs per region.
- VPCs support IPv4 and IPv6 Address allocation
- VPCs use only Private IPv4 address from the RFC1819 ranges (10/8, 172.16/12 and 192.168/16); on the other hand IPv6 address uses a global routable (Global Unicast Address) IPv6 address from AWS IPv6 address block.
- A VPC can have an IPv4 CIDR of /16 as a maximum and /28 as a minimum.
VPC and AWS Services
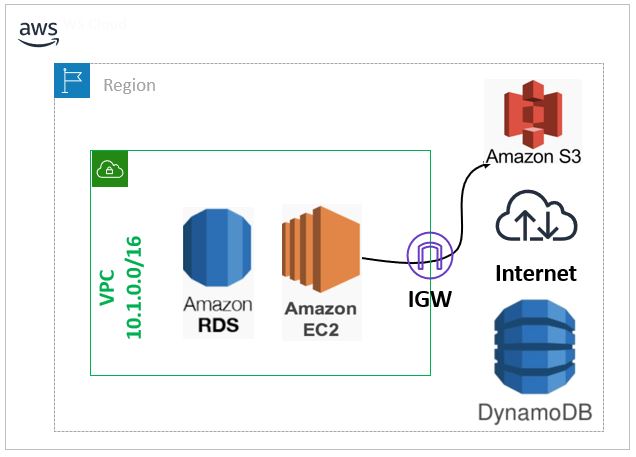
Not all AWS services are enclosed within the VPC, some of AWS services lies completely within a VPC like AWS EC2, AWS RDS, and AWS ECS while other services like AWS S3 and AWS DynamoDB are not within the VPC scope however they lie within the same region.
So in order for the resources inside the VPC to access external Resources (external AWS services or the Internet), the traffic goes through an IGW (Internet Gateway) which is a highly available Router attached to the VPC and provide Outbound Internet Access to the resources within the VPC.
The below diagram outlines how the different AWS services are positioned within a VPC and how they communicate with external resources using the IGW.
Subnet
We now understand that a VPC is a region-specific construct, so how can we choose the specific AZ within a region to deploy our workloads? This is the main role of the Subnet construct. The Subnet within AWS is bound to a specific AZ (there is a one to one mapping between an AZ and a Subnet). The below diagram outline the interaction between a VPC, Subnet, and AZ.
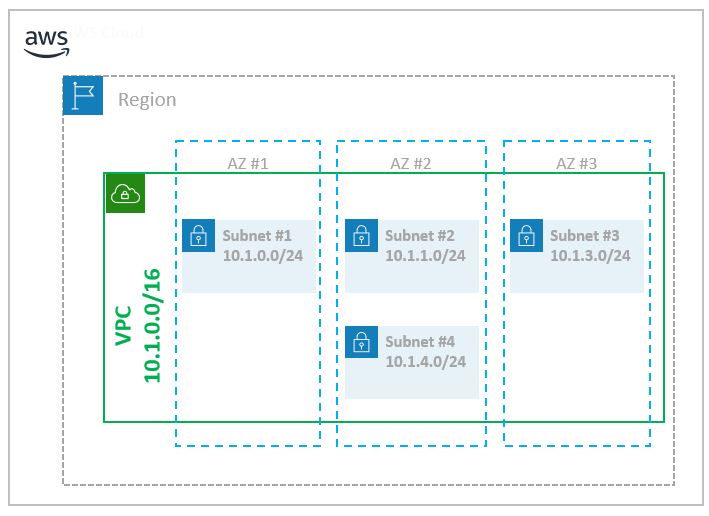
Below is a summary for the main characteristics of an AWS Subnet
- There is a one to one mapping between an AZ and a Subnet.
- A subnet is contained with a single VPC.
- We can have one or more Subnets per AZ.
- The IPv4 prefix of a Subnet must be contained within the larger VPC IPv4 CIDR.
Each Subnet should be associated with a Route Table which control the how traffic exit the Subnet. If a route table is not associated with the subnet the subnet is associated with the VPC Route Table (Default Route Table).
Conclusion
In this post, we have outlined the major networking related components in AWS and discussed how they interact in order to provide the basic networking support similar to traditional Data Center networking designs.
In the next post, we will explain how to build such components using infrastructure as a code approach with Ansible.we will also have a deep dive into on how to provision resources inside a VPCs.